Author: Derek Mizak
-
How to secure passwords – why multi-factor authentication?
Why passwords are every company’s one of the biggest risks? Personal passwords should be a concern for a security manager in every company. Managers need to prepare Identity management policies, password policies and there is a lot of items which needs to be taken into account. You can ask why.…
-
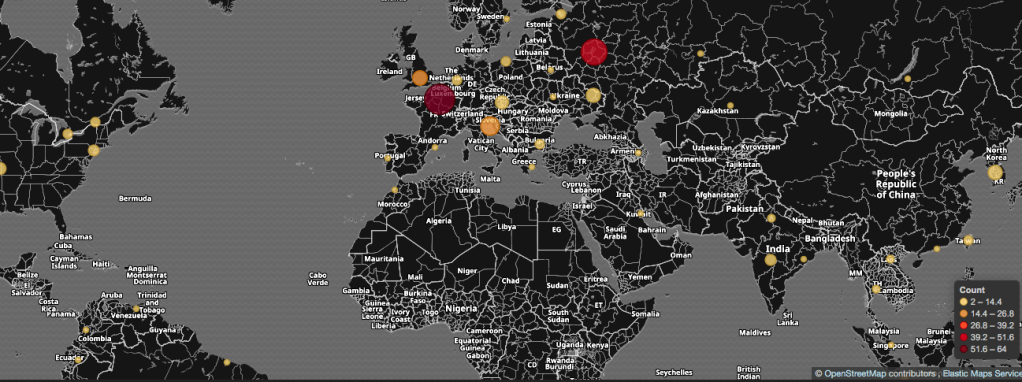
Know your enemy – lessons from IDS portal
Majority of cyber attacks come from China – our threat hunting systems are showing that more than 80% detected malicious traffic come from this direction
-

9% of users phished in less than 3 hours. Is phishing all about human behaviour?
Phishing exploit human nature by tricking unsuspected users to click a link and enter some data – usually their username and passwords into something looking innocent – we all know that. It is all about human nature and not about technology. In one of hour test phishing campaigns, 9% of…
-

GDPR – an alternative approach
Can we approach GDPR in the easy to understand way – possibly. Implementation of privacy regulation GDPR explain in the simplest possible way – we can help with aspects which you cannot implement in house.
-
The biggest threat to cybersecurity
Reflecting on some recent cyber security incidents, I thought it of benefit to write a very simple guide on how to ‘stay safe’ – back to the basics, i.e. no admin rights, application whitelisting etc. My purpose was to bring to mind those typical threats, e.g. shell-code injection, phishing, ransomware…
-

Cybersecurity Awareness Campaign
Regardless of how advanced the technological protective measures are, often the weakest part of any Information Security Management System is people or end users. It is critical to ensure that all staff and management are trained and aware of potential risks and are equipped with the necessary cyber safety skills…
-

Cyber risk landscape is changing
Advanced Persistent Threat – ATP – enforce changes to the approach to cybersecurity – we can help with transformation.
-

How we help SaaS vendors
As an SaaS vendor, the core of your operation is to provide your customers with a Web service you have developed. We have worked with a number of SaaS Vendors securing and protecting their services from cyber security threats and challenges, using our Red and Blue Team Approach. The Military…
-

Importance of awareness
A serious security incident is a question of “when”, not “if”. In 2016 we have seen a number of remarkable news bulletins about cybersecurity incidents. For example, recently we saw a very serious issue relating to the American presidential election, which resulted in sanctions imposed on Russia as an alleged…
-

Is firewall and antivirus enough?
Years ago the security of IT systems was focused on antivirus and firewalls. However, it is important to understand that antivirus was only able to detect and analyse processes which were running on specific hosts, and firewalls were just opening traffic to a specific port whilst blocking another. When malware…
You must be logged in to post a comment.