Category: Risk Management
-
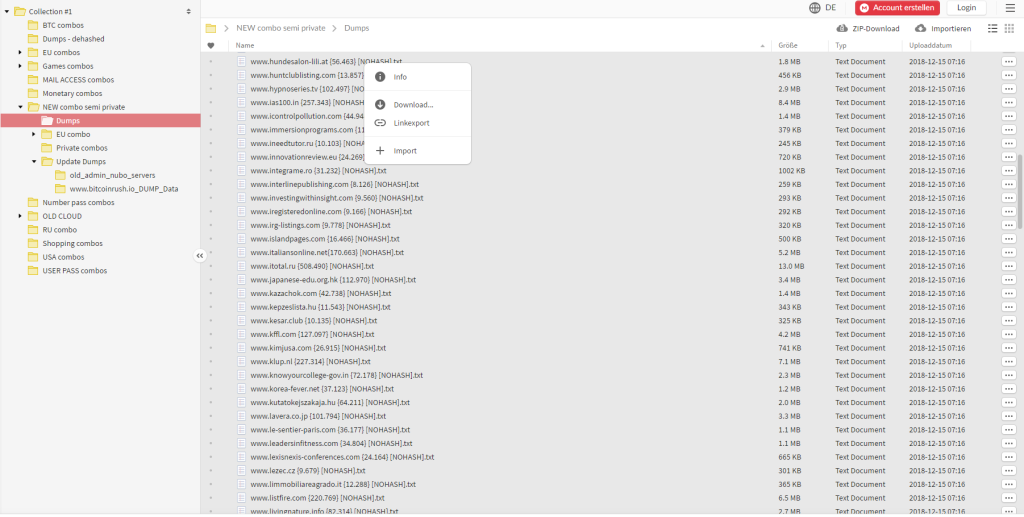
How to secure passwords – why multi-factor authentication?
Why passwords are every company’s one of the biggest risks? Personal passwords should be a concern for a security manager in every company. Managers need to prepare Identity management policies, password policies and there is a lot of items which needs to be taken into account. You can ask why.…
-
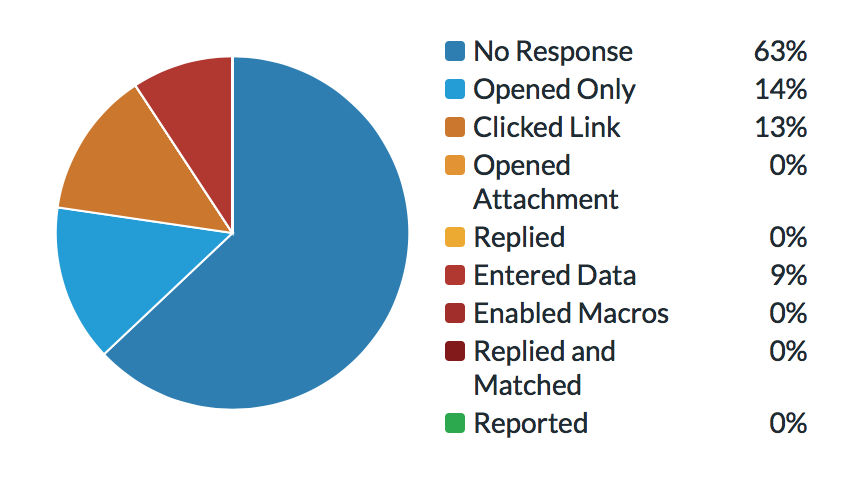
9% of users phished in less than 3 hours. Is phishing all about human behaviour?
Phishing exploit human nature by tricking unsuspected users to click a link and enter some data – usually their username and passwords into something looking innocent – we all know that. It is all about human nature and not about technology. In one of hour test phishing campaigns, 9% of…
-

Cybersecurity Awareness Campaign
Regardless of how advanced the technological protective measures are, often the weakest part of any Information Security Management System is people or end users. It is critical to ensure that all staff and management are trained and aware of potential risks and are equipped with the necessary cyber safety skills…
-

When lack of risk assessment means less money
Over the course of several months, and during our discussions with various board members, ‘cyber security’ is often compared to an insurance policy, in that it is a requirement due to fear or compliance reasons. Some directors argue that an improved cyber security position is not generating more money.…
-

Risk in code reuse
We all have to become more efficient in everything what we do or get extinct like dinosaurs – except that in our case we will be replaced by more efficient competition or even potentially by machines. In everything we do, we have to follow more with less principle all the…
You must be logged in to post a comment.